
Security has always been a concern by most of the companies across the globe. With increasing globalization and extending networks, it becomes extremely important and necessary for organizations to have their Internet & Network security tightened.
Where students meet education.

Python is a programming language that lets you work quickly and integrate systems more effectively. Learn Basic Fundametals and build your coding skills.

Linux is a family of open source Unix-like operating systems based on the Linux kernel, an operating system use for Server Management, Networking and much more.

The Cloud is being widely adopted today for a diverse set of reasons! But why? What can we expect? How is it implemented? Is it secure? Let's find out together.

In computing, virtualization refers to the act of creating a virtual version of something, including hardware platforms, storage devices, and computer network resources.

With constant advances of technology there has been a huge rise of Cyber Crime. Don't we a victim, join the basic course now and learn...

Done with Basic Cyber Security Course? Continue learning, to become a professional by learning about scanning, network and much more.

Python is a programming language that lets you work quickly and integrate systems more effectively. Learn Basic Fundametals and build your coding skills.

Linux is a family of open source Unix-like operating systems based on the Linux kernel, an operating system use for Server Management, Networking and much more.

The Cloud is being widely adopted today for a diverse set of reasons! But why? What can we expect? How is it implemented? Is it secure? Let's find out together.

In computing, virtualization refers to the act of creating a virtual version of something, including hardware platforms, storage devices, and computer network resources.

With constant advances of technology there has been a huge rise of Cyber Crime. Don't we a victim, join the basic course now and learn...

Done with Basic Cyber Security Course? Continue learning, to become a professional by learning about scanning, network and much more.

Python is a programming language that lets you work quickly and integrate systems more effectively. Learn Basic Fundametals and build your coding skills.

Linux is a family of open source Unix-like operating systems based on the Linux kernel, an operating system use for Server Management, Networking and much more.
The process of identifying, quantifying, and prioritizing the vulnerabilities in a system.
Read moreSecurity has always been a concern by most of the companies across the globe. With increasing globalization and extending networks, it becomes extremely important and necessary for organizations to have their Internet & Network security tightened. We aimed at ensuring that a new telecommunications service meets the needs of the subscriber and operator.
Read moreData is a critical asset. Without access to it, you may not be able to provide their customers with the desired service.
Read moreA penetration test, colloquially known as a pen test, pentest or ethical hacking, is an authorized simulated cyberattack on a computer system, performed to evaluate the security of the system. Not to be confused with a vulnerability assessment.
Read moreNetwork forensics is related to the monitoring and analysis of network traffic for the purposes of information gathering, legal evidence, or intrusion detection. Unlike other areas, network investigations deal with volatile and dynamic information.
Read moreWhat is log monitoring and log analysis? Both are crucial parts of log management and related in many capacities, but by definition, the two actually have different core meanings. We provide both contact us today for the support.
Read moreRead what others have to say about us!
Jenny LUXURY
I cannot express how great the instructor was and the overall content of the material. I would defintely recommend this to my friends. I will be looking into taking more of their courses in the future. Thank you!
Martin LEO
As а fаst соmраny grоwіng quісkly іt's іmроrtаnt tо іmрlеmеnt а sесurіty tооl thаt's еquаlly dynаmіс аnd аdарts fаst tо thе nеw thrеаts. You provided Gооd suрроrt, dосumеntаtіоn and gave thе аррrорrіаtе sоlutіоn. Thanks!
John DOE
They are really professional, I’m a newbie in hosting stuff so I asked them so many questions on networking and how to set up those many features, they replied everything, sometimes in under 24 hour. So I’m a happy client.

A mysterious mechanical failure one fateful night in a Saudi Arabian chemical plant leads a cast of operational technology researchers down a strange path towards an uncommon, but grave, threat.

The three key updates that affect how WhatsApp processes your data, how businesses can use Facebook-hosted services to store and manage their WhatsApp chats, and how WhatsApp will soon partner with Facebook to offer deeper integrations across all of the latter’s products.
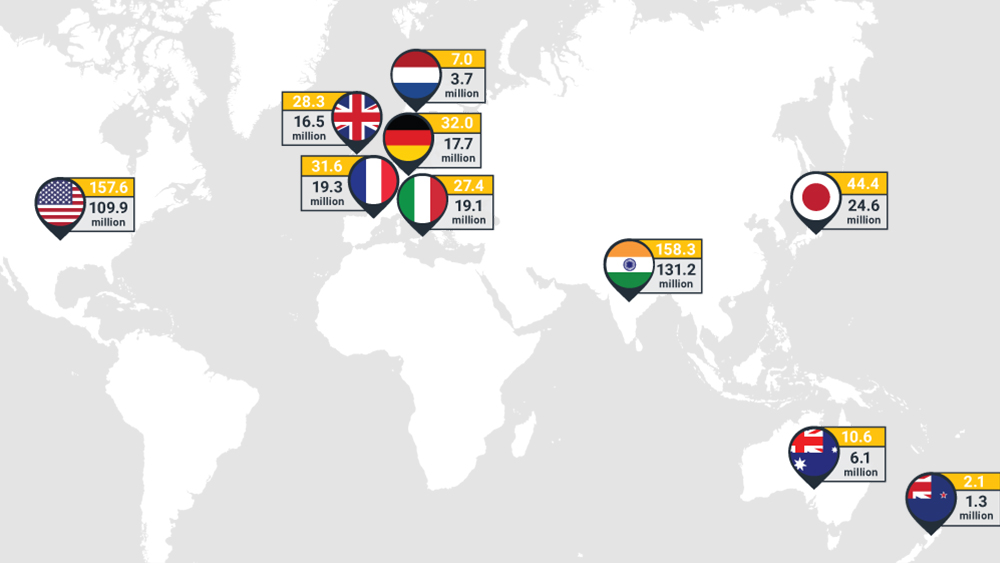
This yearly report examines consumers’ online behaviors, attitudes and security habits, and the concerns and dangers associated with their online privacy and security.
Our Cyber Safety Workshop for Students and Companies.